Implementing the principle of least privilege
Get credential governance with role-based access controls and zero-trust security with Zoho Vault.


What is the principle of least privilege?
Organizations often struggle to balance providing employees with the necessary access to perform their jobs effectively while preventing unauthorized access to sensitive information. The principle of least privilege (PoLP) offers a solution by granting employees only the minimum permissions required to fulfill their duties.
By limiting access to only what is essential, PoLP significantly reduces the potential for unauthorized access, both from malicious insiders and external threat actors who may compromise employee credentials. This proactive approach helps safeguard sensitive data and protects the organization's overall security posture.
The benefits of the principle of least privilege
If an HR employee has access to the human resources management system to update employee records but also holds unnecessary permissions to IT infrastructure, the risk of a data breach increases substantially if their account is compromised.
Reduce the attack surface
By restricting user permissions, the potential for unauthorized access and data breaches is significantly reduced.
Minimize exploit impacts
Even if a hacker gains unauthorized access, the PoLP restricts the potential damage by confining the accessible resources.
Support regulatory compliance
Frameworks like GDPR and HIPAA require stringent access controls. Applying PoLP ensures that users only have access to the essential systems and data, helping organizations meet these regulatory requirements.
Enhance security in hybrid work environments
With employees often accessing sensitive data remotely, maintaining strict access controls is crucial. Enforcing the PoLP decreases the security risks linked to remote work.

Principle of least privilege and Zero Trust security
Zero Trust security is a modern security approach based on assuming that any user or device could be a potential threat. Unlike traditional security models, which typically trust all connections within an internal network, Zero Trust treats every access or connection request as untrusted until proven otherwise.
Zero Trust is connected to PoLP in many ways. It enforces strict access controls and permissions, ensuring that users are granted only the minimum access necessary to perform their tasks. This rigorous verification process extends the core idea of PoLP, emphasizing that no one should have more access than they need, regardless of their origin or position.
Simplifying credential governance through Zoho Vault
- Account management
- Access governance
- Audits and reports
- Disaster recovery
- Enterprise readiness
Account management
Fine-grained controls
Set granular controls to restrict user and group access to specific features, ensuring more precise privilege management.
Explore more
Policy enforcement and password resets
Enforce strict password guidelines and expiration dates to safeguard sensitive data and prevent unauthorized access.
Explore more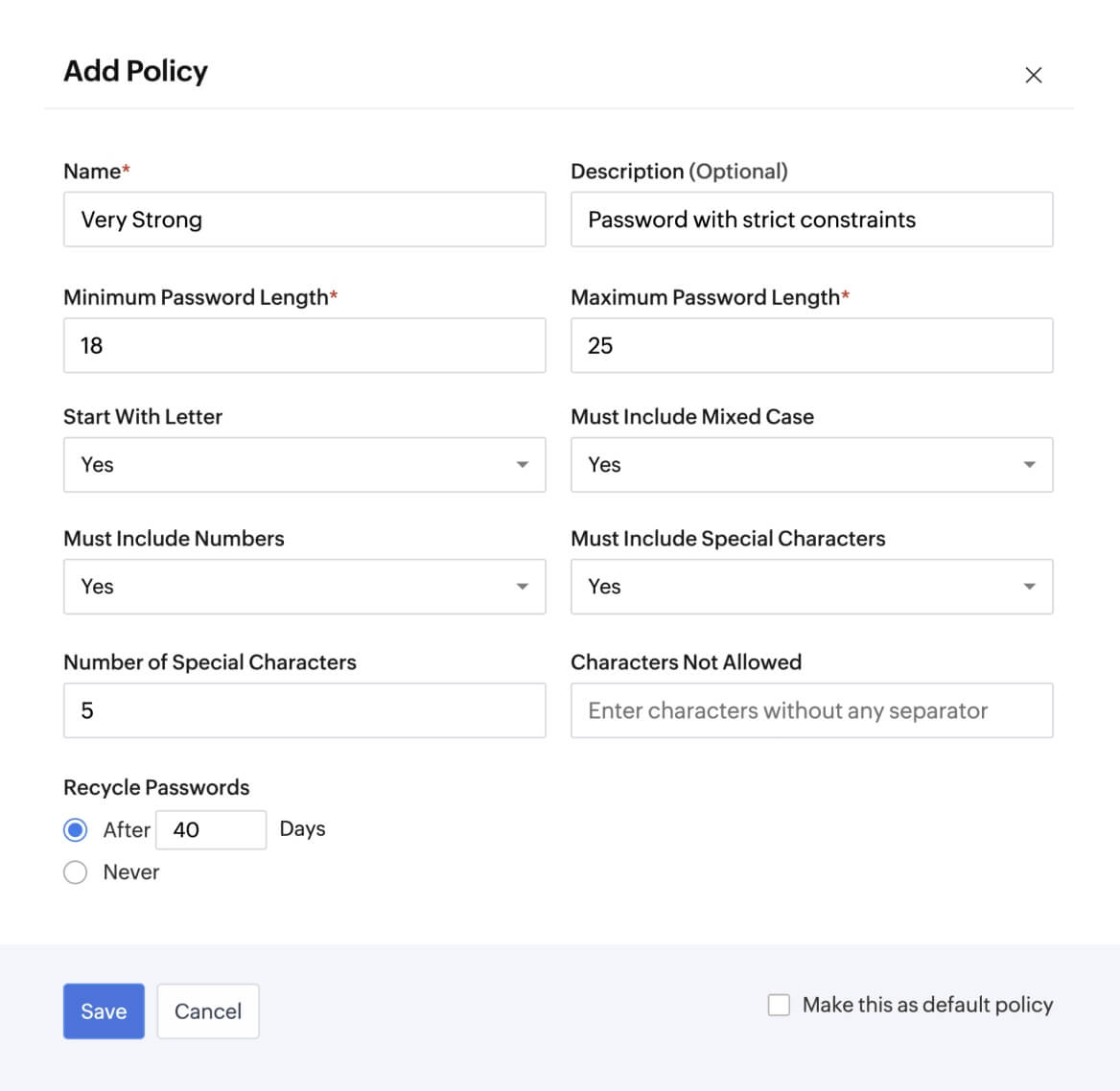


Access governance
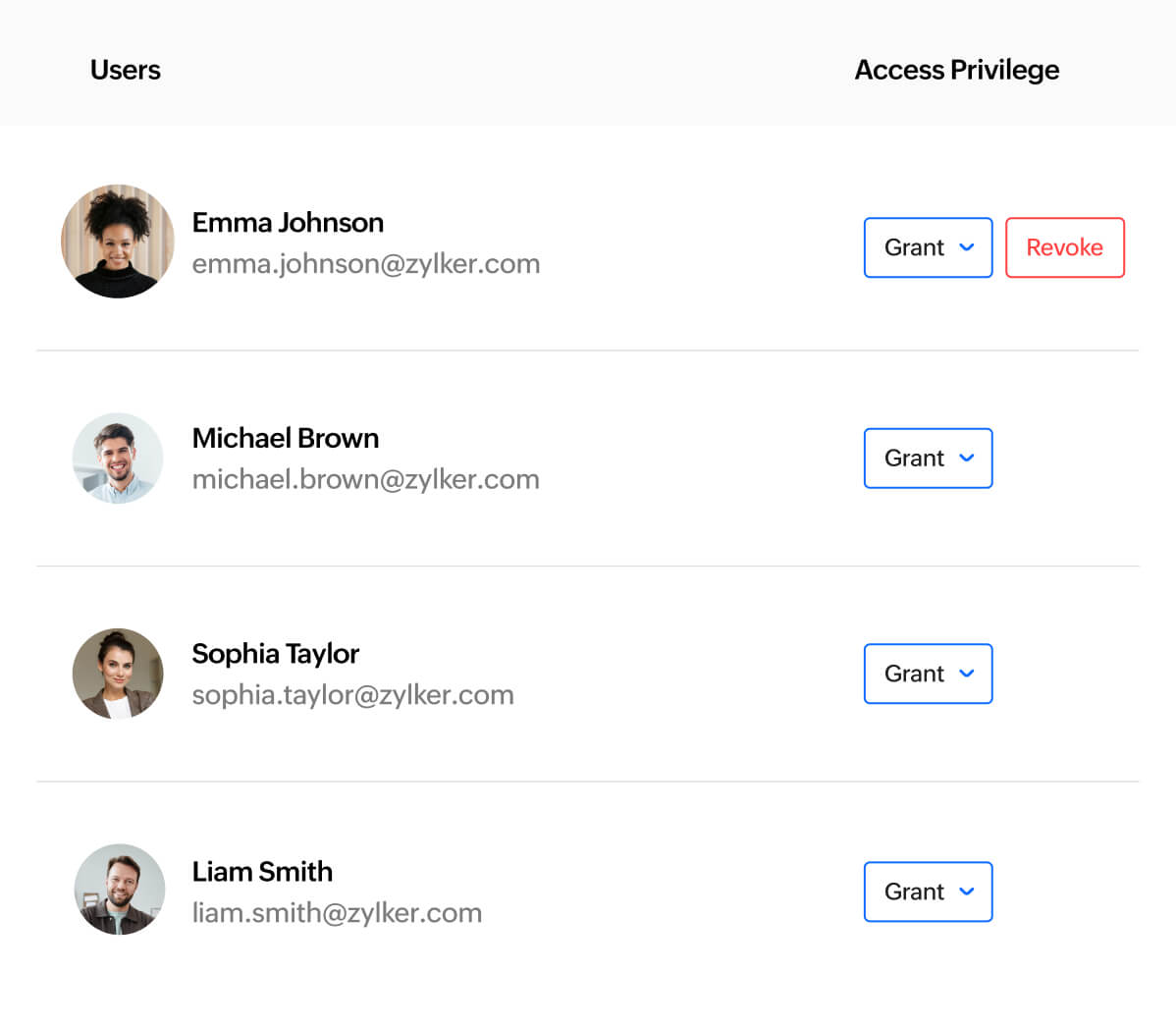
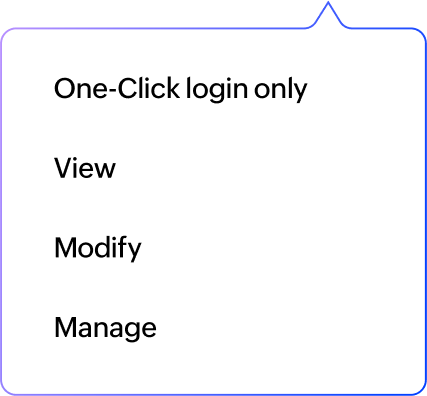
Role-based access controls (RBAC)
Enforce the principle of least privilege by granting users access to sensitive credentials based on their roles and requirements and revoking them when access is no longer needed.
Explore more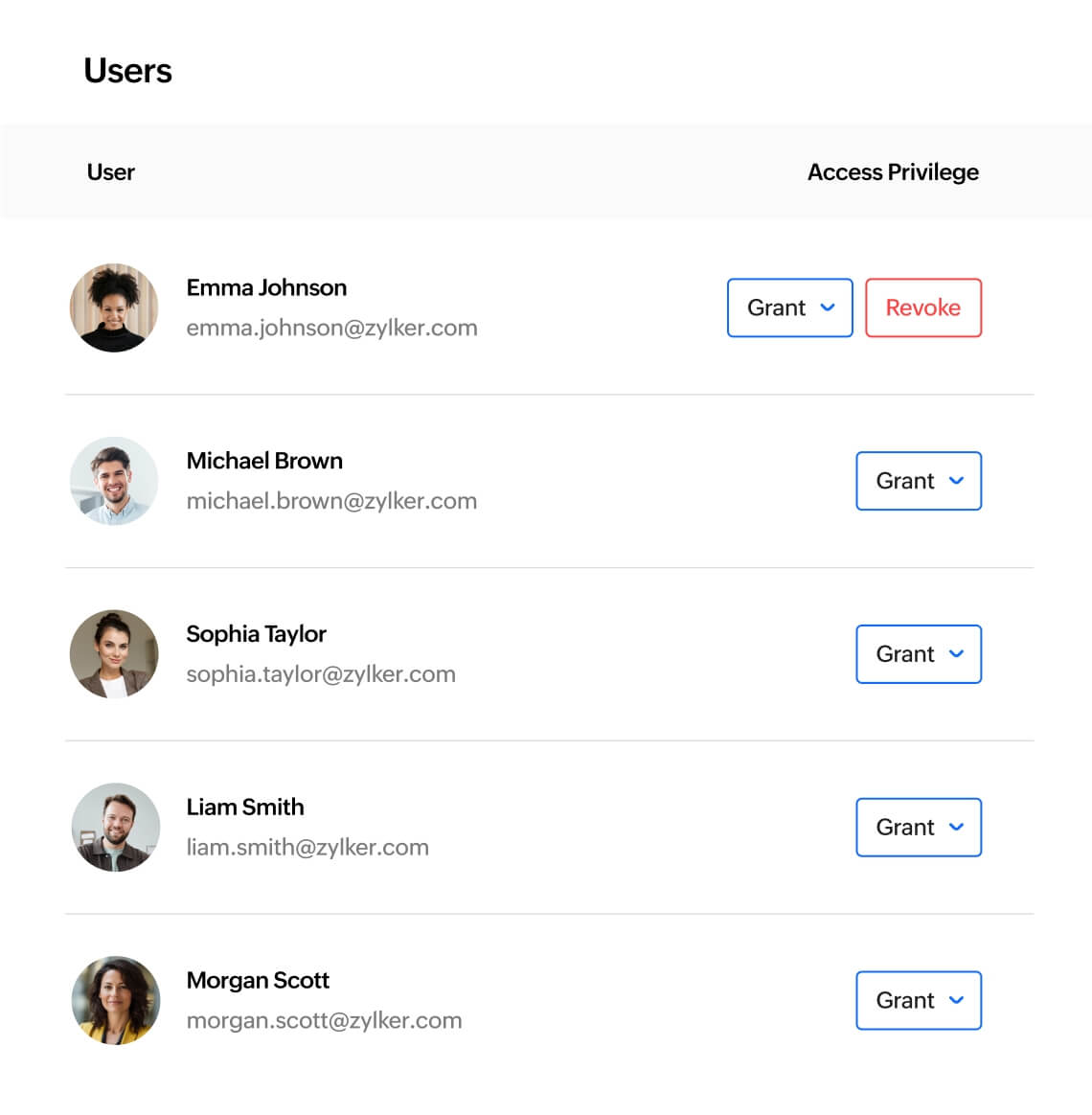
Password request-release workflows
Control access to sensitive shared credentials with request-release workflows. Automate the password access and approval process through advanced workflows.
Explore more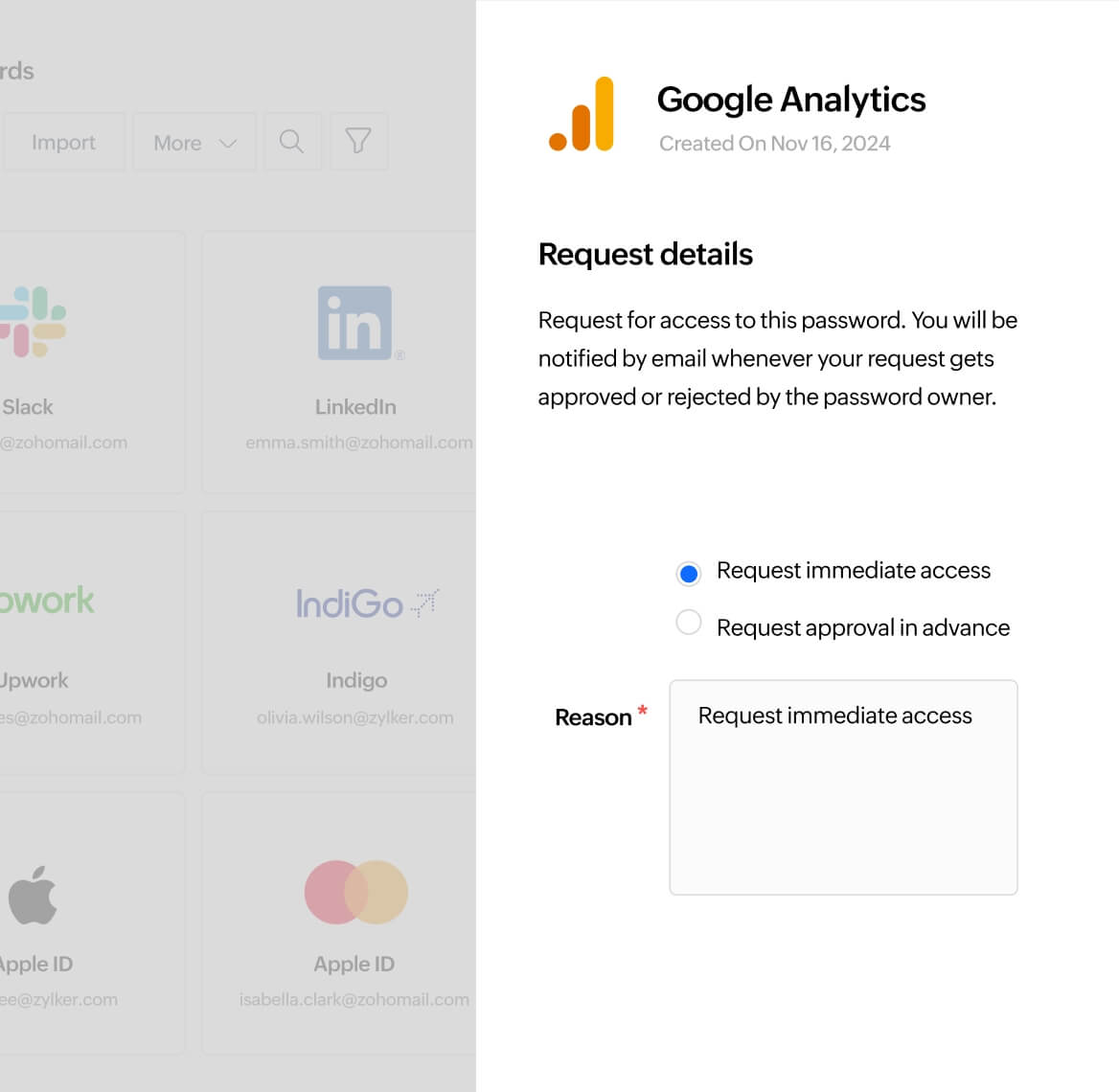


Audits and reports
Real-time audit trails
Track user activities and detect suspicious activities with real-time audit trails. Receive instant notifications and monitor access across your organization.
Explore more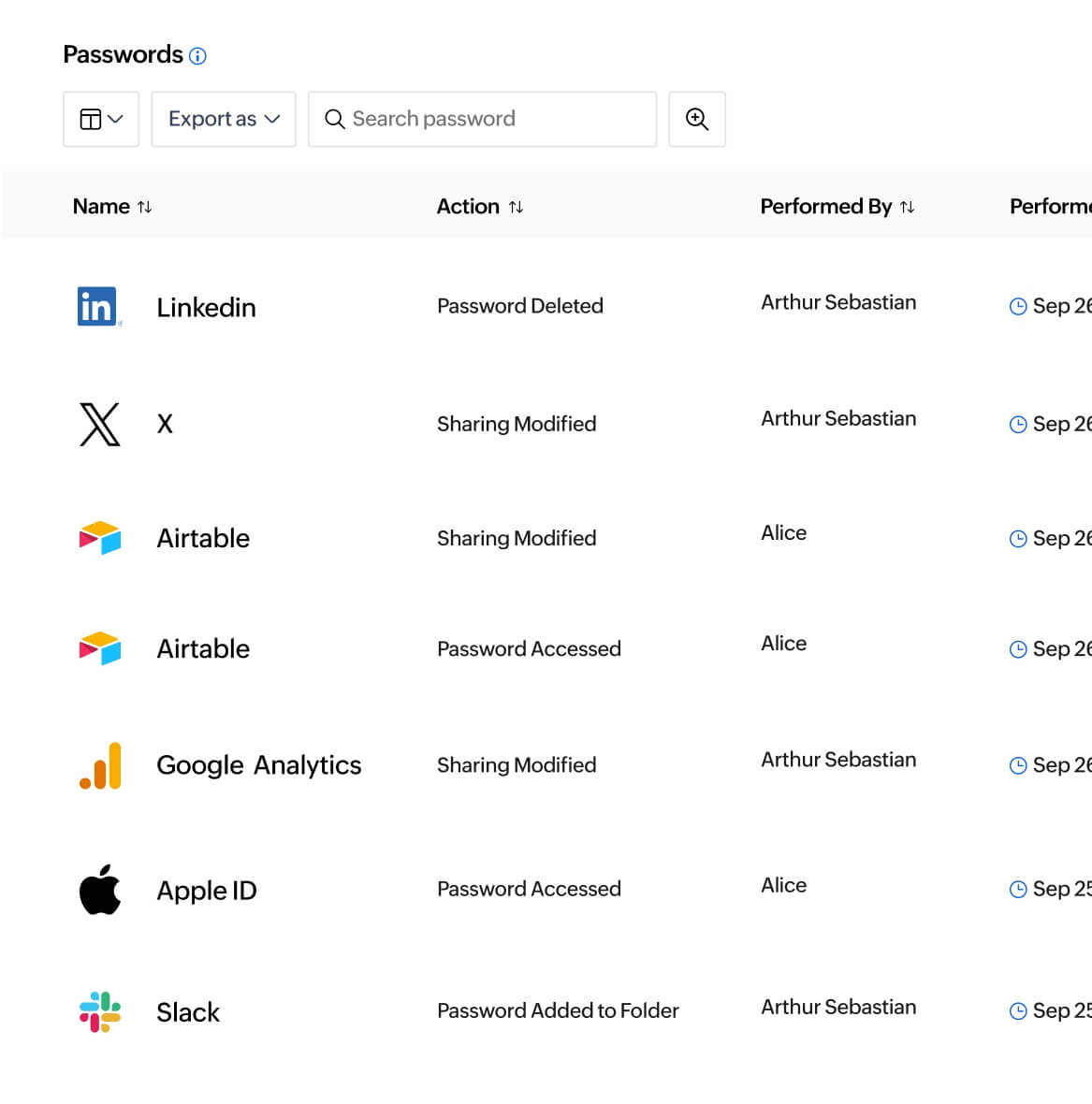
Intuitive reports
Make informed business decisions with detailed user access and activity reports. Ensure adherence to industry-leading security and compliance frameworks through out-of-the-box, real-time reporting.
Explore more


Disaster recovery
Emergency access
Set up emergency mechanisms to guarantee access to your credentials and controls during challenging situations.
Explore more
Offline access
Ensure continued password availability with Zoho Vault's offline access. Download your passwords as an encrypted HTML file and securely access them from anywhere.
Explore more


Enterprise readiness
Secure password vault
Store your sensitive passwords securely in a centralized vault, safeguarded with AES-256 encryption.
Explore more
Multi-factor authentication
Enhance account security and deter unauthorized access with multi-factor authentication.
Explore more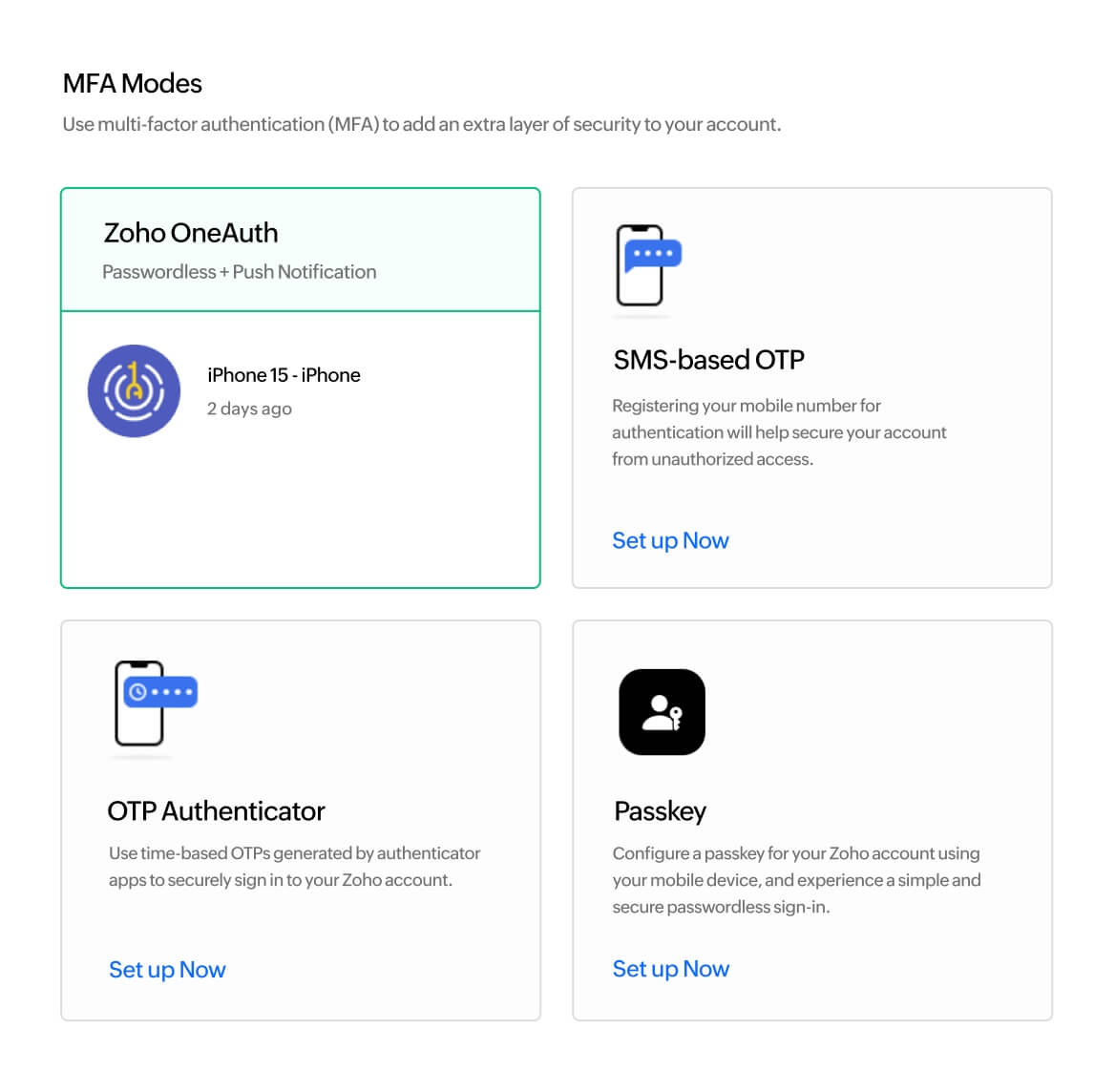


Straightforward path to meet compliance
Least-privilege enforcement offers organizations a streamlined path to compliance. By limiting user access to only the resources necessary for their roles, it provides granular visibility into who accessed what and when, facilitating audits and demonstrating adherence to regulatory standards. This approach is essential for meeting industry and federal requirements like HIPAA, GDPR, and CCPA, which demand stringent access control measures to protect data integrity and system security.



Frequently Asked Questions
How does the PoLP help organizations defend against advanced persistent threats and sophisticated cyberattacks?
Enforcing the PoLP restricts user access rights to only what is necessary, reducing the impact of compromised credentials in a breach. This approach limits an attacker's lateral movement within the network, preventing privilege escalation and effectively mitigating APTs and sophisticated cyberattacks.
How does adhering to the PoLP enhance regulatory compliance and data privacy risk management?
What are the challenges of implementing the PoLP?
Grant only what's necessary.
Secure the rest